Migrating from Wordpress to Hugo Part 4: Securing the Site with SSL
I originally drafted this in June 2018. Following on from Sam McGeown's recent migration to Hugo, I thought I'd finally publish this in case it's useful for anyone rather than sitting on it until I complete the process!
Why SSL?
It's only a blog, so why SSL? It's going to be static content, so why SSL?
In this article I'll deal with those questions and go through the process of requesting an SSL certificate using AWS Certificate Manager.
Let's Go Secure!
If you recall, our finishing point is going to end up being a collection of static HTML files served out by AWS. There's nothing particularly risky about serving up or requesting such static files, it's how the internet started out after all. What's different now though are people's perception of risk and privacy and how that's reflected in the technology we use.
Google, for example, promote SSL sites slightly higher in their search rankings than non-SSL sites and have been doing so since 2014. Some modern browsers have started flagging warnings about non-SSL sites and this will likely become more obvious over time. Users are becoming more picky and aware as a result, or perhaps they're driving the changes to an extent. SSL is here to stay though and it's worth setting it up, especially if it's free!
AWS off public SSL certificates for free. Let's go set one up!
We could either do this via the AWS console, or using the CLI. At this time I haven't worked out how to do it completely via the CLI, but I'm going to start there. (Note: Fro CloudFront, I think that the certificate has to be in the us-east-1 region regardless.)
aws acm request-certificate --domain-name mpoore.uk --subject-alternative-names www.mpoore.uk michaelpoore.com www.michaelpoore.com --validation-method DNS --idempotency-token 201806 --region us-east-1
This command will requests a new SSL certificate with a subject name of “mpoore.uk” and alternative names of “www.mpoore.uk”, “michaelpoore.com” and “www.michaelpoore.com”. The validation method of DNS will require us to validate that we own the domain by making certain DNS entries.
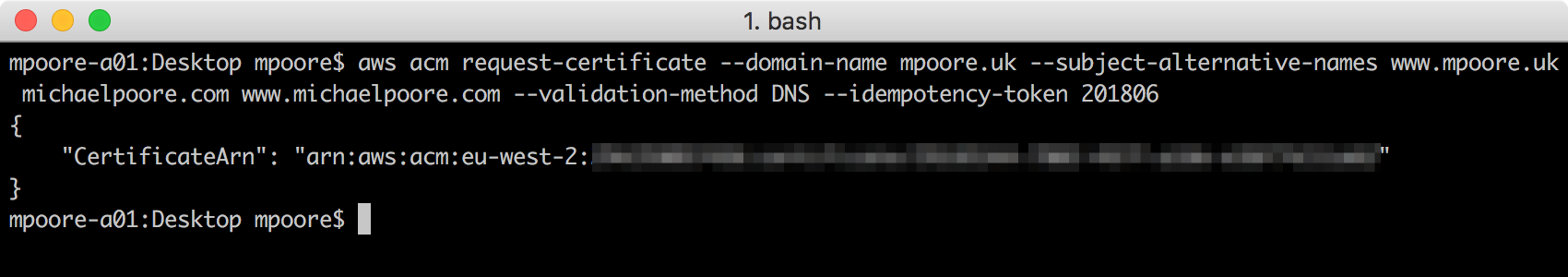
What you get back, is the reference to the certificate. I'll need that later.
Looking at the AWS Console though, you'll see that the certificate is not yet issued and must be validated.
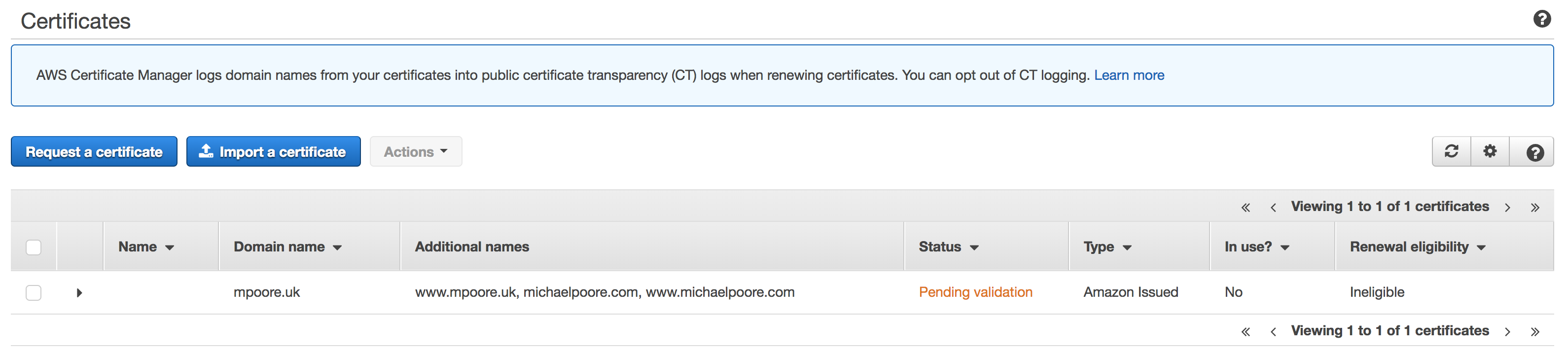
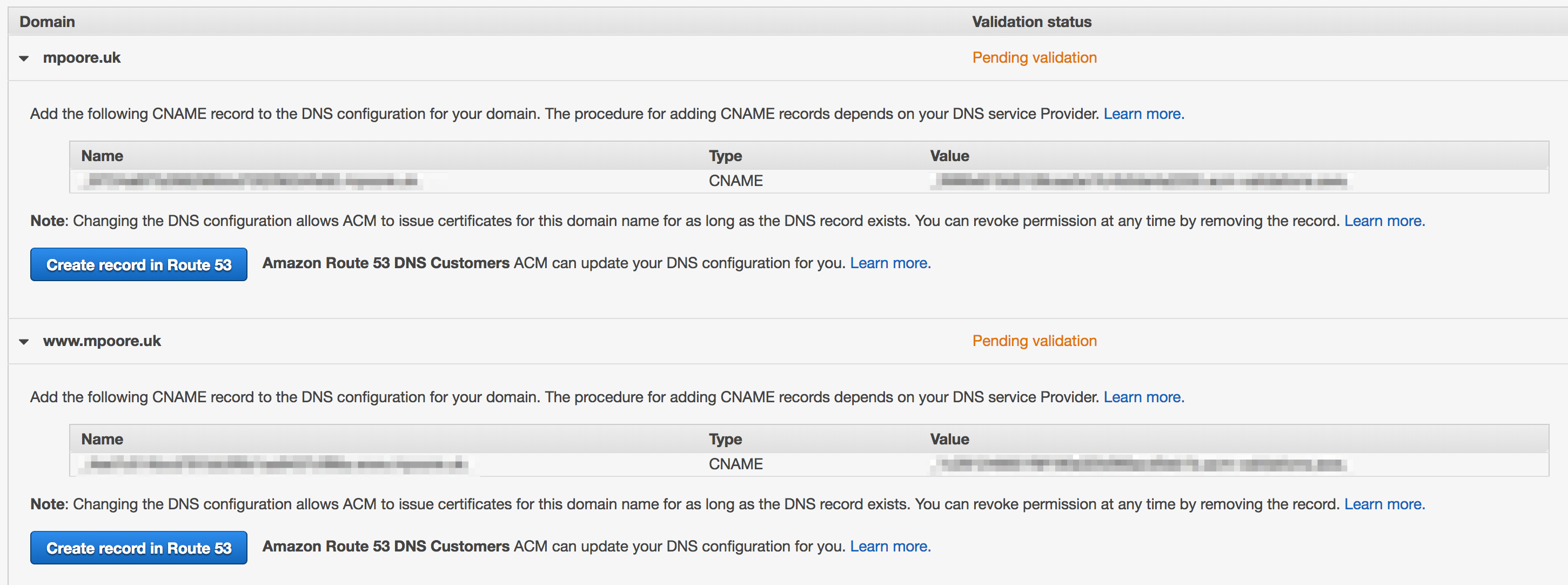
To validate each of the domains in the certificate, you need to get some DNS CNAMEs created. Luckily, for mpoore.uk there's a button for that. For michaelpoore.com though, I had to do these manually as the DNS for that is still with 1&1 for the time being.
Once they're all done, the validation will eventually complete and the certificate will be issued. Just save the certificate ARN value from earlier as it'll be needed later.
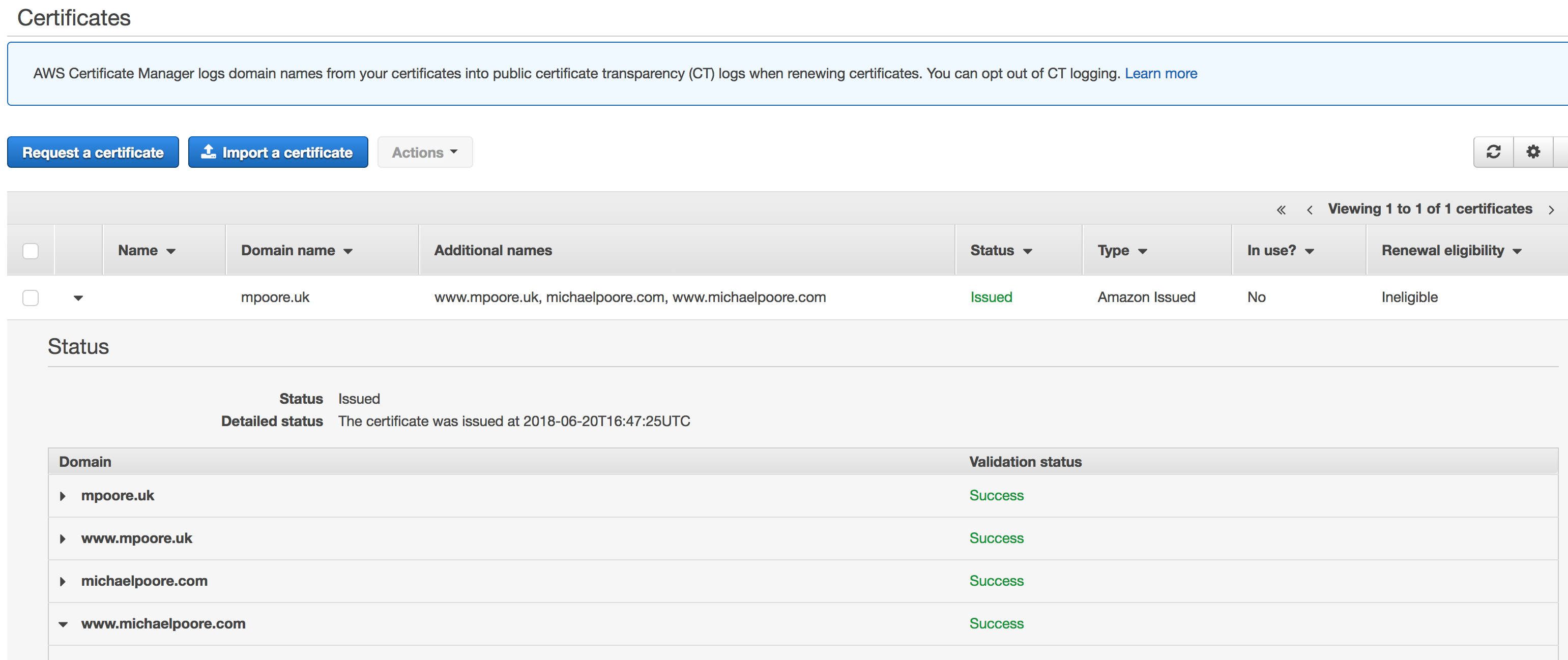
Sadly, this is as far as I got in the process before other things (life, eh) got in the way. I will be back to revisit and complete the the process though.
